Request filtering
You can filter out unwanted visitor identifications using the request filtering rules. To do this, navigate to the App settings -> Request Filtering section of the dashboard. You can filter requests by website origin, request headers, and mobile apps.
For details on how to configure request filtering for mobile apps, check out this article:
Website origin filtering
You can either whitelist or blacklist websites that use your application API Key. To do this, click Configure in the Websites section.
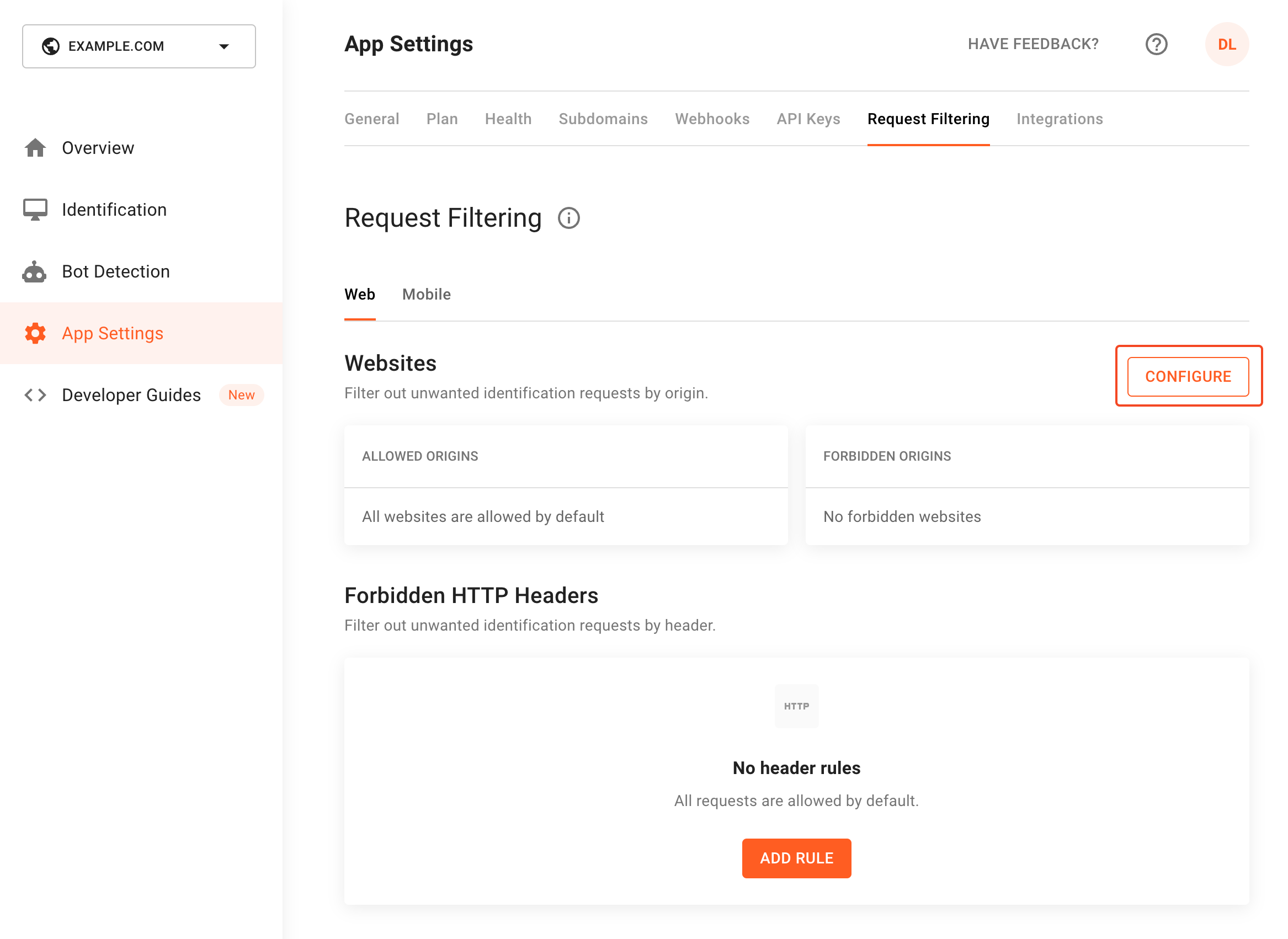
Screenshot of how to configure request filtering in the FingerprintJS dashboard
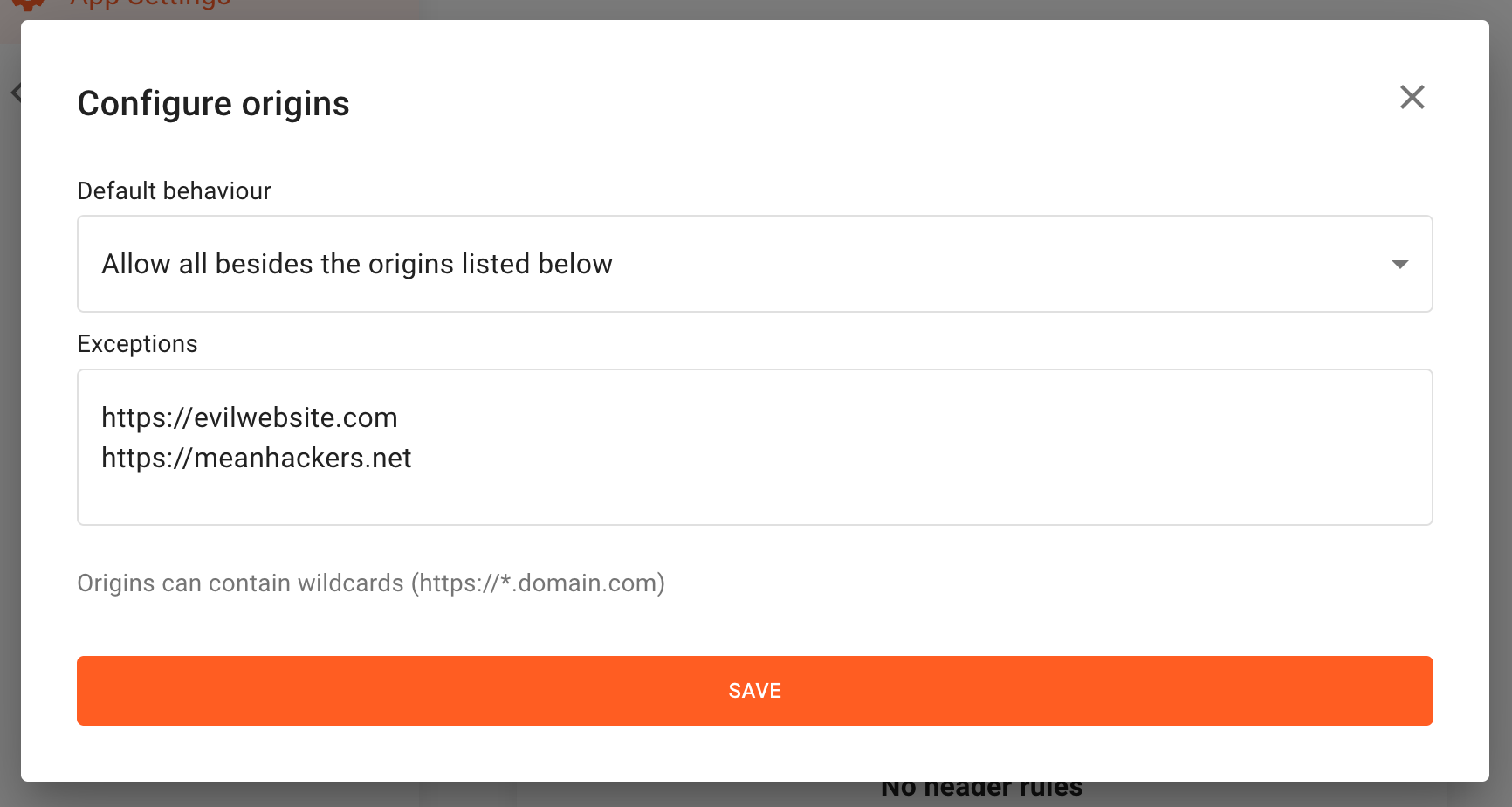
Blacklisting
Blacklisting is best used for FingerprintJS clients that need to allow a large number of origins to use their API key. Origins that are suspected of API key-stealing can be blacklisted, preventing that select list from running up your bill.
1 - Click on Configure to open the configuration panel.
2 - Select Allow all besides origins listed below as default behavior.
3 - Fill the Exceptions field with the list of blacklisted origins.
A website origin is defined by the scheme and the domain name of the URL used to access it.
You can use the wildcard character (*) as a subdomain name.
Screenshot of the form required to set up origin filtering
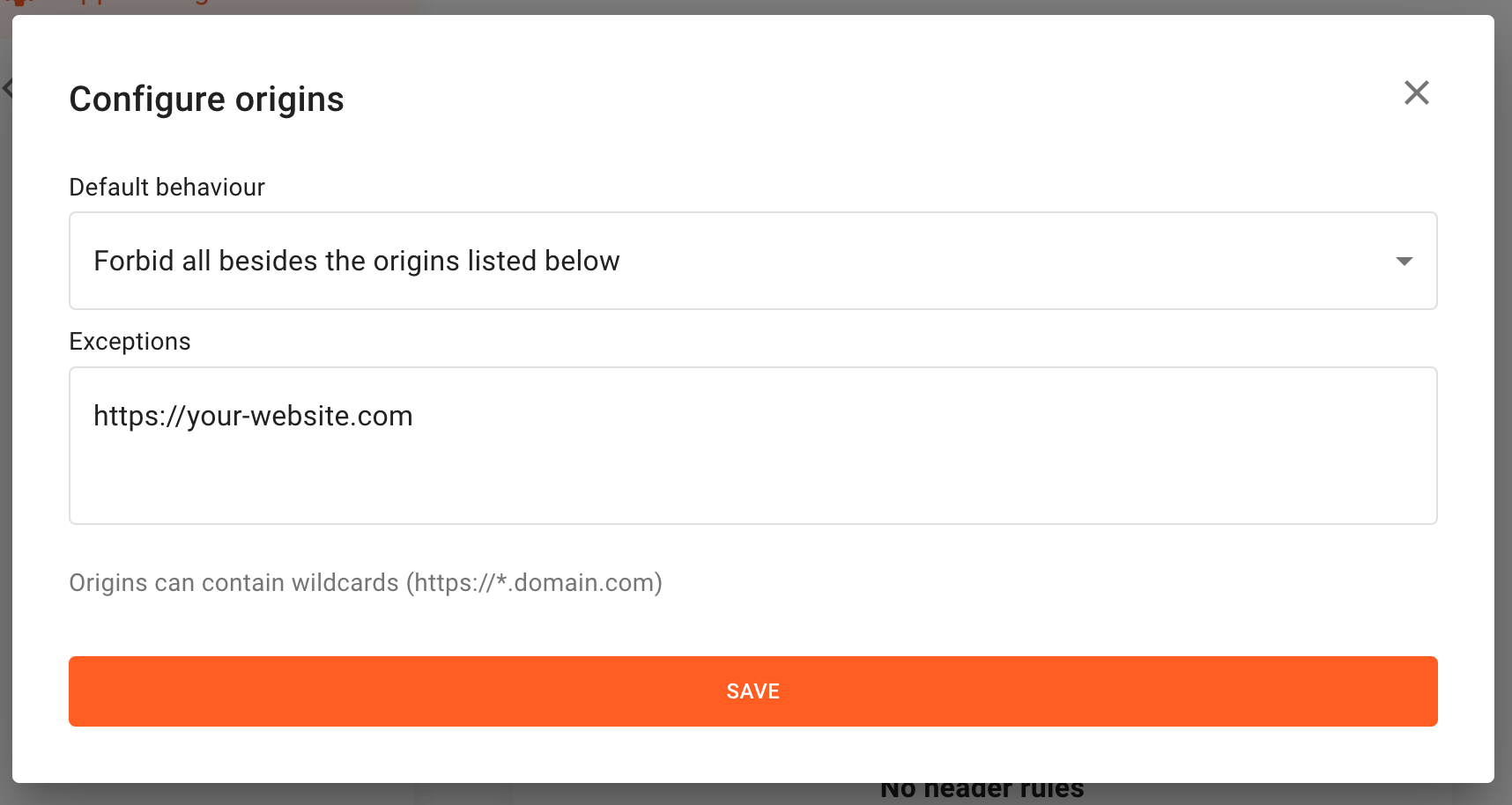
Whitelisting
Whitelisting is best used for Fingerprint clients who only want a select few origins to use their API key. Whitelisting prevents API key-stealing by only allowing the select origins API key access.
1 - Click on Configure to open the configuration panel.
2 - Select Forbid all besides origins listed below as default behavior.
3 - Fill the Exceptions field with the list of whitelisted origins.
Screenshot of the form required to set up origin whitelisting
HTTP header filtering
In some cases it is useful to filter out identification requests by HTTP headers. Identifications that you might want to filter out include server-side rendering applications, crawlers, search indexing bots, or website availability monitors.
Fingerprint ignores some popular bots such as Googlebot, Bingbot, DuckDuckBot, and others by default and does not bill for those requests. This behavior is available on the Pro plan only.
To create a new header rule, go into the Request Filtering section of the dashboard and click on the Add Rule button to the right of the Forbidden HTTP Headers section title.
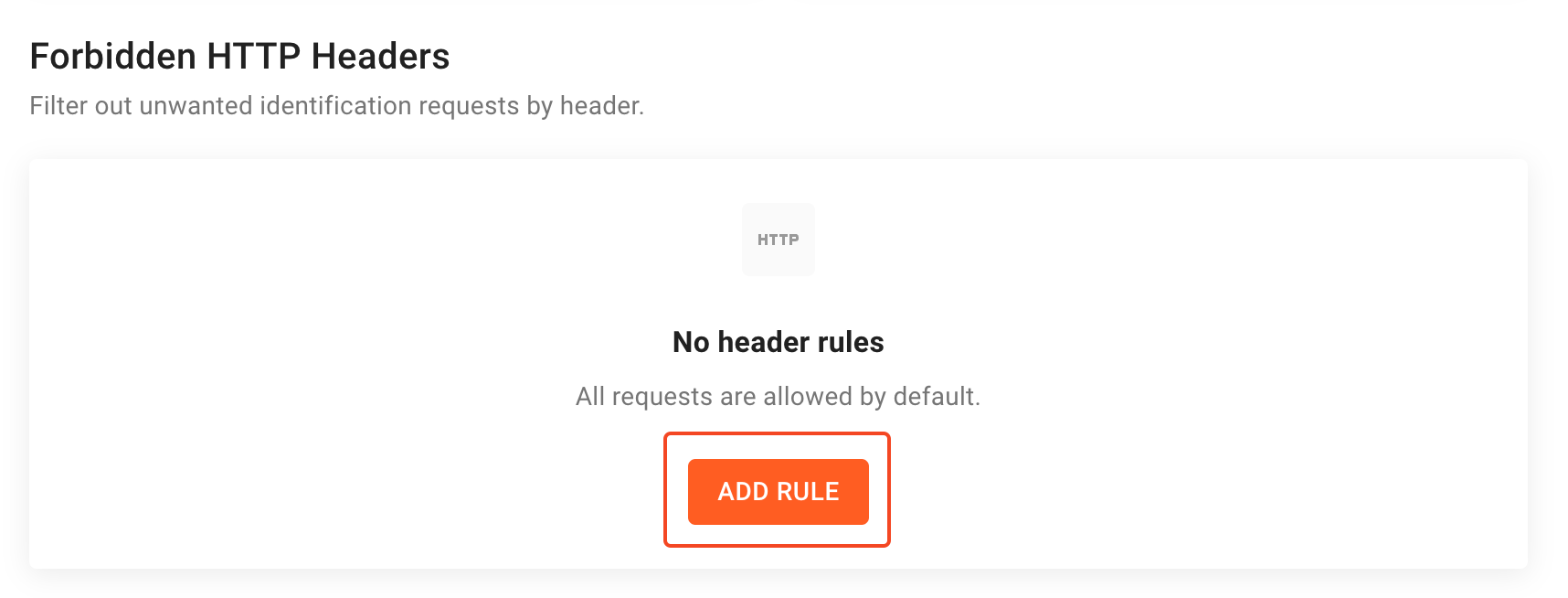
Screenshot of where to configure forbidden HTTP headers in the Fingerprint dashboard
A header rule is determined by the Header name, Match Rule, and Value.
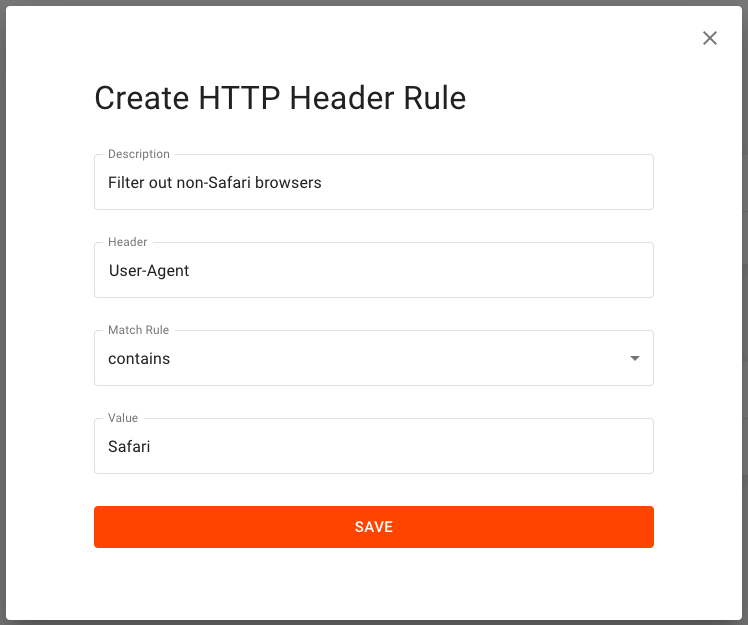
Screenshot of the form required to create an HTTP header rule
Keep in mind that the regular expression (regex) match rule is defined by RE2 notation.
Consider using the Regex101.com tool to obtain regular expression match rule strings:
1 - Open this link.
2 - Select the Golang Flavor option on the left panel.
3 - Debug the regular expression to suit your needs.
4 - Copy the regular expression string and paste it into the value field as-is.
Update policy and rule priority
It can take up to 5 minutes to start filtering incoming requests after creating or editing a website or header rule.
Origins rules are checked first and HTTP header rules are checked second.
Billable identification requests are performed each time your application invokes the
FingerprintJS.get()method of the JS agent.
Updated 22 days ago
